The funny part of modern technology is that it is so deeply integrated with our daily lives that we don’t even notice where or how we leave traces of our digital lives. And it’s not even a question of if, since we use computers to buy goods online, interact with people on social media, store personal photos, and more. As such the hard drive inside the computer is likely to record a lot of sensitive data, covering the likes of social security numbers, income, addresses, credit card numbers, and everything in between. Add in the fact that we usually take pictures of family and friends and someone with access to the storage medium is able to draw a complete picture of our life.

And don’t fall into the trap of thinking that you have nothing to hide because that makes you the perfect target. If you want to keep your private data to yourself, then it’s wise to follow some basic data security and privacy protection rules when selling an old computer or donating a hard drive. As a quick example, imagine a hardware security company randomly purchased 20 used hard disks from eBay, ran data recovery software and found a treasure trove of data that was worth some serious money on the dark web of the internet, perhaps identifying a lawyer’s former hard drive containing:

Without getting into too much detail of what could be found on a family laptop, you can still get the point. Not everyone knows how to properly delete data stored on their hard drives, but the answer is pretty simple: use dedicated software or hardware to perform the task.
When you think about it, the storage medium was designed to perform a single job: to store the data you last wrote on it to retrieve later. But deleting this data doesn’t remove it from the drive, meaning that it can still be recovered by someone with the right know how. Here’s how you can properly delete data from storage disk, and since hard disk drives and solid-state drives need different handling, we’ll talk about them separately.
If you know how hard drives and data management on such storage mediums work, then you are already aware that simply deleting a file doesn’t remove it from the disk. Instead, it updates a table containing all the files and their locations by removing the pointers to their logical addresses so from the operating system’s perspective the locations that were previously occupied by the deleted files are now free.
The only way a user can ensure the data is removed and can’t be revived is by overwriting it. Since Secure Delete is not enough in this case, there is software designed for proper “hard drive sanitization”, the industry term for securely removing data.
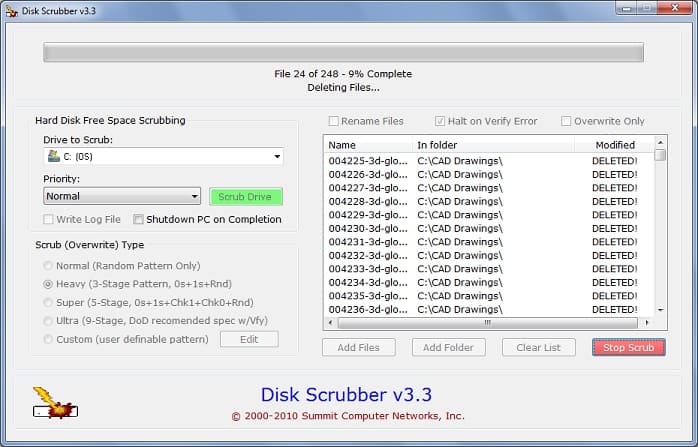
There is a wide range of such software for Windows, with the likes of free Microsoft utility SDelete or other third-party tools like Eraser, Hard Disk Scrubber, or Darik’s Boot And Nuke. What these apps will do is overwrite the data still existing on the selected drive with random data, binary digits of zeroes and ones.

The other method is by deploying hardware to do the job. Wiebetech’s Drive Erazer Ultra, StarTech Hard Drive eraser and others are highly effective at wiping drives clean simply by attaching the drive to the tool, but these are more costly than a software license.
Things get a bit more complicated with solid-state drives (SSDs) because there are differences in how they store and remove data. If we add the fact that SSDs impose serious policies on data destruction and therefore limiting the likelihood of data recovery via software, then you get the main idea behind the difference. If you delete a file from an SSD and don’t have any software such as Disk Drill’s Guaranteed Recovery, then you won’t be able to retrieve it.

Still, there are utilities we recommend using in addition to encryption to make sure that the data is overwritten before selling a computer or its hardware. These are tools developed by the manufacturers of SSDs, so they can be trusted.
From a privacy perspective, encrypting an SSD makes sense, and as of writing this seems to be the most secure way to protect your data. Encrypting it ensures that no one except for you, the keeper of the secret key, can gain access to the data.
Share your thoughts, ask questions, and connect with other users. Your feedback helps our community make better decisions.
©2012-2025 Best Reviews, a clovio brand –
All rights
reserved