
Randomly generated time-based two-factor authentication codes or ‘2FA codes’ have become a part of various login processes. They represent an extra layer of security designed to ensure that the rightful user is the only person who can access an account, even if someone else somehow knows the password.
You may already be familiar with 2FA codes: they are the ephemeral six-digit numbers generated by physical tokens issued by the bank, for example, or the ones you’ll need to remember when using the Google Authenticator app. Theoretically these numbers are randomly generated, but are they truly random or do they have any easily identifiable pattern that could be discovered by a vigilant eye?
2FA codes are everywhere: from banking apps to email, any service that cares about user protection will have already implemented this secondary layer of security with the first layer being the familiar username and password. The most popular use of this extra layer is the with one-time passwords (OTP), which essentially means a six-digit code sent…
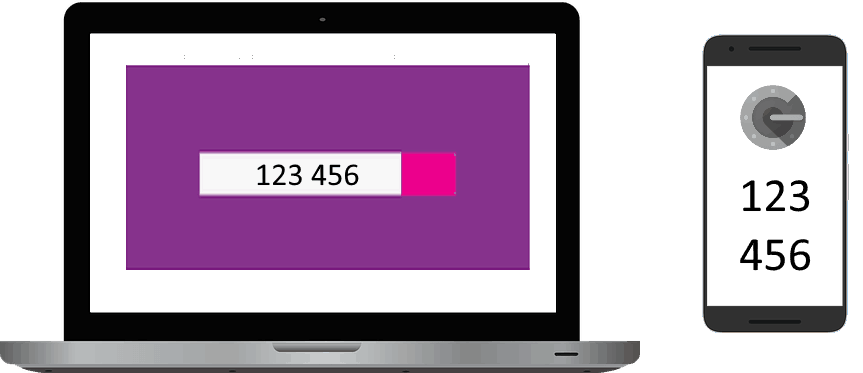
At the heart of this security layer is the Time-based One-time Password algorithm (TOTP), which computes a six-digit code (the one-time password) using a shared secret key at the time of log in. The six-digit passcode is usually valid for 30 seconds, so users have a half-minute window to remember and enter the code into the required field.
The TOTP has been adopted as the standard and is used by a variety of two-factor authentication systems. The interesting fact about these six-digit codes is that the core of such code generation is recommended to be random, but it doesn’t actually have to be that way. It’s okay to pick a cryptographically secure pseudorandom generator that is “properly seeded with a random value,” as suggested by the documentations.
The reason for using pseudorandom generators comes from the nature of how random generators work. For example, when Apple introduced the shuffle feature into iTunes it used a truly random generator that put together a playlist for the user. The problem was that this truly random generator could easily group multiple songs from the same artist together, which triggered complaints from users. This led to Apple making the feature less random to end up feeling more random. That’s how pseudorandom generators took over random generators.
For some reason – maybe because of our intuitive sense – humans are incapable of accepting randomness as it is. For example, we might tend to notice a pattern in 2FA codes, which makes us wonder whether these codes have a logical pattern to them to make them memorable: the majority of six-digit random numbers have at least one repeating digit, and some will have a repeating sequential digit next to each other.
It hasn’t been scientifically confirmed, but security engineers have a very good reason for using a pseudorandom number generator that is tweaked to generate passcodes that are easy to remember. One of the main reasons is to boost the adoption rate of this security layer; the sad truth is that 2FA isn’t as widespread as it should be. For example, only 10% of Google users have enabled it since its deployment due to the extra inconvenience that it adds to the login process.
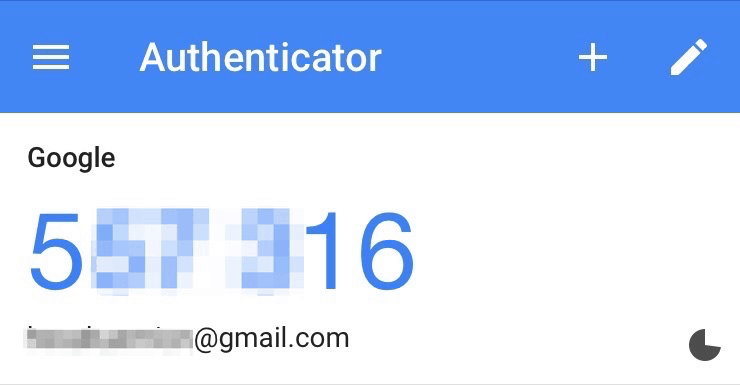
After monitoring the six-digit codes that the Google Authenticator app generates, Wired’s Robbie Gonzales started wondering whether they were generated using a trick that made them more memorable. Google says that the one-time passwords aren’t designed to be intentionally memorable, but it does omit some codes.
Google eliminates passwords that resemble the short-code phone numbers when it sends out passcodes over text message. This technically makes skipping hard-to-remember passcodes feasible. But in the end, it all depends on the user and how they perceive that six-digit string. For various reasons, humans are likely to find memorable patterns, even in a random string of numbers.
Share your thoughts, ask questions, and connect with other users. Your feedback helps our community make better decisions.
©2012-2025 Best Reviews, a clovio brand –
All rights
reserved